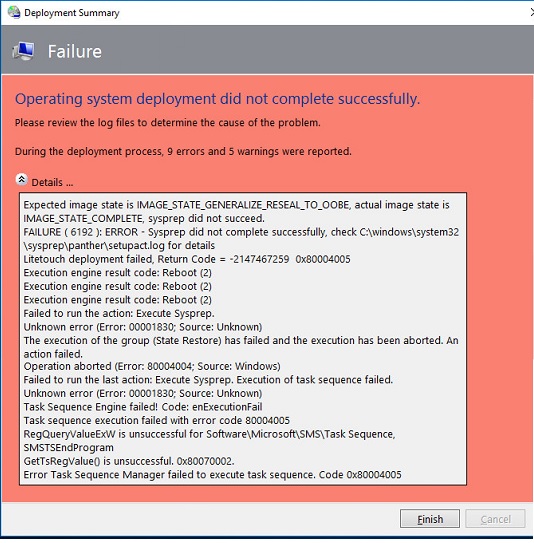
We recently came across an issue creating a Task Sequence to capture an installation of Windows 10 with MDT 2013 Update 2. During the Sysprep task, the following error was displayed:
The C:\Windows\system32\sysprep\panther\setupact.log was reviewed and based on the log entries shown below, we determined that the root cause of the error was the Store Apps being updating during the capture process.
2016-05-24 13:26:03, Info [0x0f0080] SYSPRP ActionPlatform::LaunchModule: Found 'SysprepGeneralizeValidate' in C:\Windows\System32\AppxSysprep.dll; executing it 2016-05-24 13:26:03, Info SYSPRP Entering SysprepGeneralizeValidate (Appx) - validating whether all apps are also provisioned. 2016-05-24 13:26:05, Error SYSPRP Package Microsoft.WindowsAlarms_10.1510.12020.0_x64__8wekyb3d8bbwe was installed for a user, but not provisioned for all users. This package will not function properly in the sysprep image. 2016-05-24 13:26:05, Error SYSPRP Failed to remove apps for the current user: 0x80073cf2. 2016-05-24 13:26:05, Error SYSPRP Exit code of RemoveAllApps thread was 0x3cf2. 2016-05-24 13:26:05, Error [0x0f0082] SYSPRP ActionPlatform::LaunchModule: Failure occurred while executing 'SysprepGeneralizeValidate' from C:\Windows\System32\AppxSysprep.dll; dwRet = 0x3cf2 2016-05-24 13:26:05, Error SYSPRP SysprepSession::Validate: Error in validating actions from C:\Windows\System32\Sysprep\ActionFiles\Generalize.xml; dwRet = 0x3cf2 2016-05-24 13:26:05, Error SYSPRP RunPlatformActions:Failed while validating SysprepSession actions; dwRet = 0x3cf2 2016-05-24 13:26:05, Error [0x0f0070] SYSPRP RunExternalDlls:An error occurred while running registry sysprep DLLs, halting sysprep execution. dwRet = 0x3cf2 2016-05-24 13:26:05, Error [0x0f00d8] SYSPRP WinMain:Hit failure while pre-validate sysprep generalize internal providers; hr = 0x80073cf2
Since MDT uses the local administrator account to run the task sequence, the updates were being incorporated in the local administrator account’s profile and preventing Sysprep from “generalizing”.
The fix was to add a registry key that disabled the Store Apps from updating:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsStore\WindowsUpdate] "AutoDownload"=dword:00000002
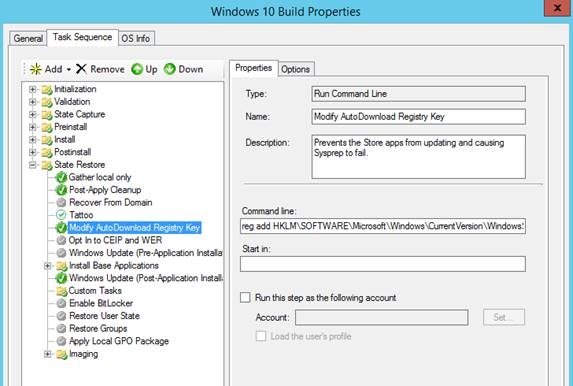
We created a Command Line task to create the registry key.
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsStore\WindowsUpdate /v AutoDownload /t REG_DWORD /d 2 /f
The task was added into the State Restore phase just after the Tattoo task.
This shouldn’t be an issue when creating a capture Task Sequence with Configuration Manager since the system account is being used to execute the sequence rather than the local administrator account.