Recently Microsoft released the Local Administrator Password Solution (LAPS). This software is designed to mitigate the risk of a Pass the Hash (PtH) credential replay attack, in which a malicious entity obtains a random user’s password hash and attempts to log on using the hash instead of entering the plaintext password. LAPS helps mitigate this risk by allowing you to set and manage unique local administrator passwords for each individual workstation in your environment, thus ensuring different and short-lived hashes.
The free tool is available for download here: https://www.microsoft.com/en-us/download/details.aspx?id=46899
Installation is pretty simple. There are three parts to installation:
1. Extend your AD Schema (Creates two new attributes for storing LAPS info).
2. Configure Group Policy (allows you to configure password complexity and other items).
3. Install Client Side Extension for Group Policy on local workstations.
The installation documentation is easy to follow and gives you step-by-step instructions.
Microsoft provides a PowerShell Module that has cmdlets to allow you to automate many of these installation tasks, such as Extending the AD Schema and setting Security Permissions for who can see the Local Administrator Password Attributes.
You can heavily secure the attributes if you wish. However, if someone has access to AD to view this attribute, they would typically be someone who should have rights to that info anyway.
The Group Policy ADMX/ADML files allow you to set Password Complexity and Age. You can also specify which local administrator account you wish to manage if you are using a custom one and not the BUILTIN Administrator.
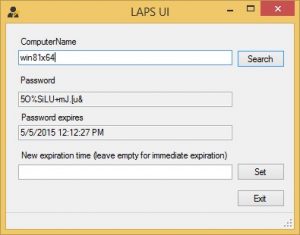
When you install the Management Tools on your server there is a convenient GUI that is included, allowing you to view the Local Administrator Password for a given workstation as well as force it to change that password via expiration of the existing one.
You can also manage this using the provided PowerShell Cmdlets as well.
Once all those are in place it takes a gpupdate /force and a reboot of the client workstation to get things rolling.