By now a lot of us have heard of the SSD hardware encryption issue that’s been reported on the blogosphere and confirmed by Microsoft. If your physical hard drive supports hardware encryption, Microsoft will use it by default–and therein lies the problem. The hardware encryption method is potentially less secure than software encryption via BitLocker. With some hardware encryption methods, the hardware vendor is essentially storing a “blank” master password, which gives easy access to the encryption key that was used to encrypt the files on the drive in the first place.
Hardware encryption is generally faster, but we do not want to sacrifice security for speed. So our problem is twofold; we need to identify any drives in our organization that may have been hardware encrypted and prevent it from happening during imaging going forward.
Here’s how to prevent SSD hardware encryption in your task sequences.
The three Registry Values to prevent the use of hardware encryption and force software encryption are as follows:
(Create a run command line step)
REG ADD HKLM\SOFTWARE\Policies\Microsoft\FVE /v FDVHardwareEncryption /t REG_DWORD /d 0 /f
REG ADD HKLM\SOFTWARE\Policies\Microsoft\FVE /v FDVAllowSoftwareEncryptionFailover /t REG_DWORD /d 0 /f
REG ADD HKLM\SOFTWARE\Policies\Microsoft\FVE /v FDVRestrictHardwareEncryptionAlgorithms /t REG_DWORD /d 0 /f
You may add them before you do BitLocker or BitLocker pre-provisioning. These registry values get created when/if you enable this policy in GPO but, as we know, those policies come after imaging and BitLocker in Configuration Manager.
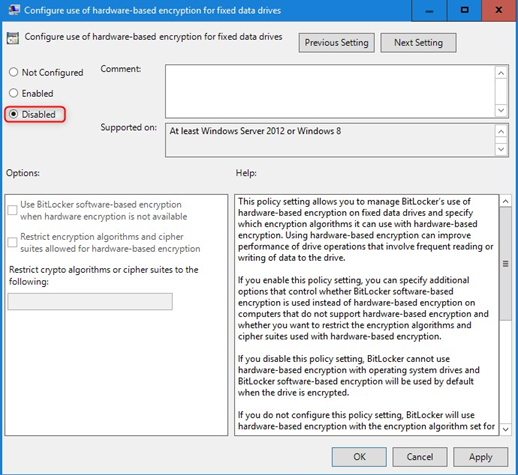
Add this to your GPO to prevent any issues in the future with any decrypt/re-encrypt scenarios:
Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption -> Fixed Data Drives
That’s great for new images, you say, but how can you check all your existing machines? You may use the power of ConfigMgr’s Scripts to produce a very basic report of all the BitLocker Encryption Methods used by a collection of machines.
A simple WMI query will grab what you need:
Write-Output (Get-WmiObject -namespace “Root\cimv2\security\MicrosoftVolumeEncryption” -Class Win32_EncryptableVolume).EncryptionMethod
This will return the numerical value based on the encryption method used (reference).
| Value | EncryptionMethod |
| 0 | None |
| 1 | AES_128_WITH_DIFFUSER |
| 2 | AES_256_WITH_DIFFUSER |
| 3 | AES_128 |
| 4 | AES_256 |
| 5 | HARDWARE_ENCRYPTION |
| 6 | XTS_AES_128 |
| 7 | XTS_AES_256 |
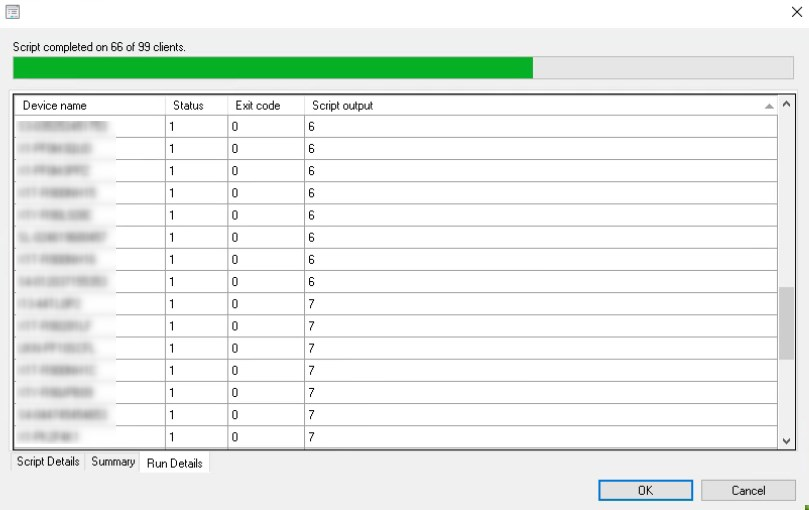
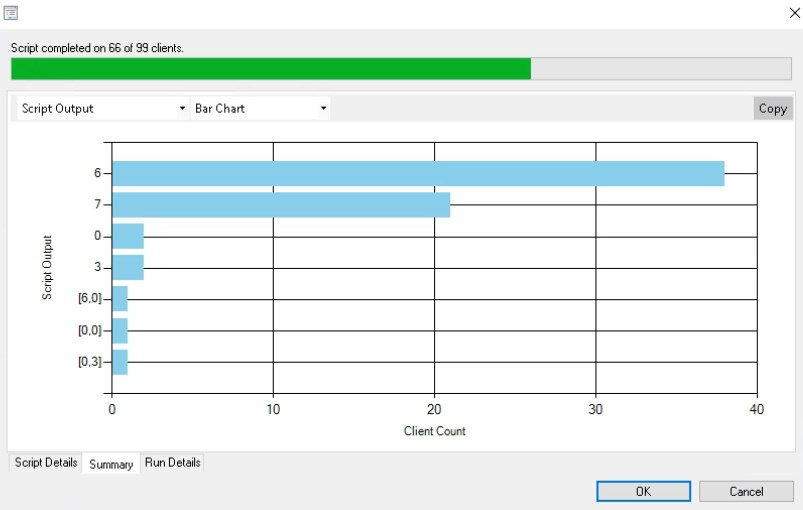
ConfigMgr will then provide a simple status report. On the run details you get the machine name and the script output. If you see any 5’s in your environment, you will need to address those via an decrypt/re-encrypt with the GPO in place.
Lastly, if you don’t see the scripts option in your ConfigMgr console, you will need to enable the feature “Create and run scripts.” This is found in the Administration node -> Overview -> Updates and Servicing -> Features.