Are you confident that the Endpoints in your environment are well protected against cyberthreats? Can you answer important questions such as “what KBs are missing?” or “how well are the network configurations secured?” We’re sharing an overview of Microsoft Defender for Endpoint, a platform the Kraft Kennedy Enterprise Client Systems team recommends leveraging to expedite remediation by providing detailed explanations of detected threats or incidents and how to address them.
Why Microsoft Defender for Endpoint Security?
When considering IT security, there are many things to worry about, including security updates and patches, anti-malware, and ransomware attacks. There are common methods used to address these concerns, traditionally relying on strong patch management by applying patches on a monthly or even weekly basis. This is not enough.
In response to the current threat landscape, Microsoft has made it easier to protect your endpoints and infrastructure against attacks and data breaches by developing an excellent enterprise endpoint security platform called Microsoft Defender for Endpoint.
Microsoft defines this tool as “an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats.”
This product answers “what KBs are missing?” or “how well are the network configurations secured?” This tool assists with remediation by providing detailed explanations of detected threats or incidents, along with the specific steps needed to address them.
How does Microsoft Defender for Endpoint work?
Defender for Endpoint uses a combination of technologies, including sensors integrated into the Windows 10 operating system that detect suspicious activity and Microsoft cloud services that leverage big data and online assets signals from Microsoft endpoints across the globe. All of that is analyzed and delivered to clients on dashboards that contain insights into the overall health of the environment as a score, threat and incident detection events, and recommendations that can be broken down to the computer or user level.
While Defender for Endpoint has multiple security features, the Threat and Vulnerability Management dashboard is the most popular. It leverages software inventory information to deliver important KPIs (Key Performance Indicators), detections, and recommendations. As shown below, it provides scores for current exposures, device configuration, and exposure distribution.
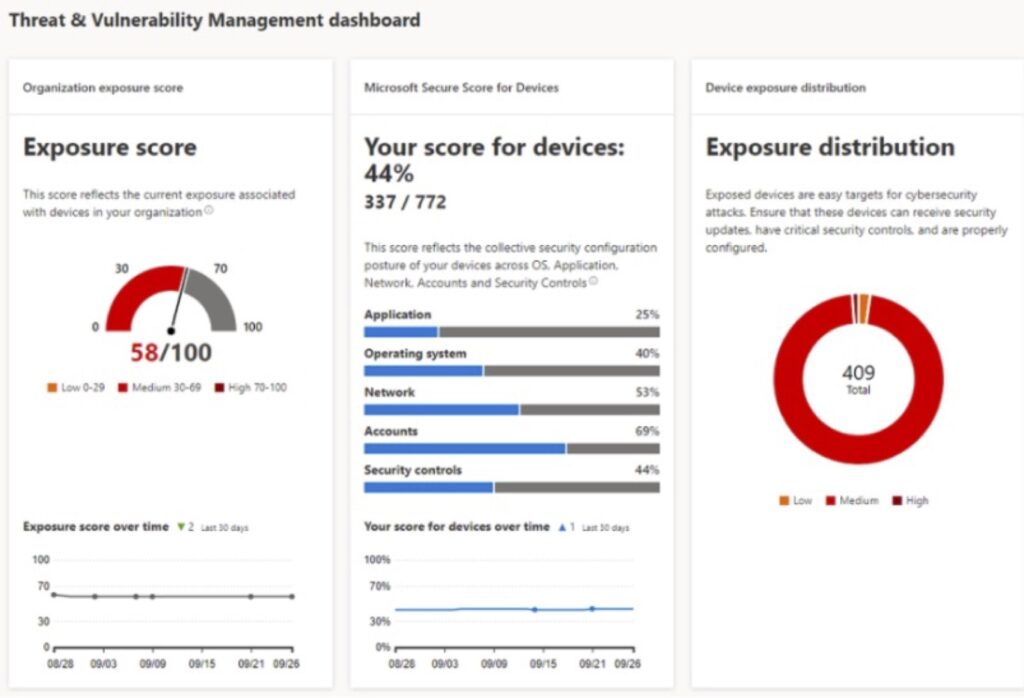
Defender for Endpoint Security Recommendations
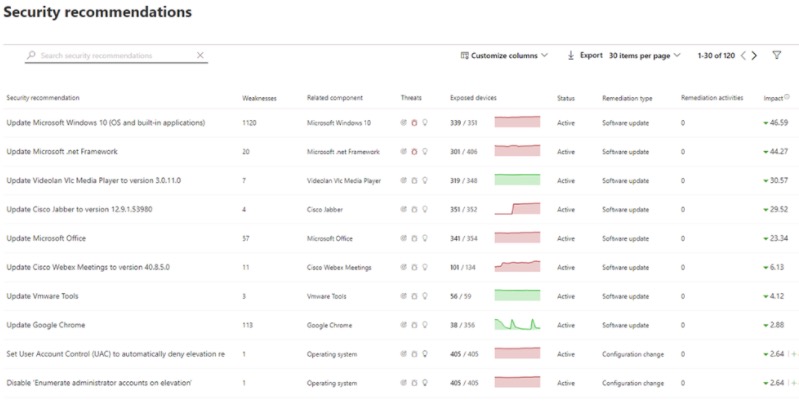
Utilizing the information provided on the security recommendations page (pictured below) can be invaluable, as it prioritizes where to focus your efforts to harden your endpoints or infrastructure. These recommendations are a result of real-time scanning of endpoints summarized as actions to mitigate the risk.
License Requirements and Supported Platforms
Licensed via any of the following: Windows 10 Enterprise E5, Microsoft 365 E5 (M365 E5), or Microsoft 365 A5.
Supported operating systems: Windows 10 (1607 or later) Windows Server (2008 R2 up to 2022), Linux, Android, and MacOS.
Recently Microsoft introduced two new standalone license plans:
- Plan 1
- This is a user subscription license with limited Defender for Endpoint features.
- Plan 2
- Available as a standalone license and includes all Defender for Endpoint features included in the Microsoft E5 plan.
What about Privacy?
Sensor data is stored in your private and isolated cloud instance that you configure when you start configuring Defender for Endpoint.
Defender Technologies Product Names
As of April 2022, Microsoft has changed the name of their Defender technologies including Advanced Threat Protection.
The new names of each product are:
- Microsoft 365 Defender (previously Microsoft Threat Protection)
- Microsoft Defender for Endpoint (previously Microsoft Defender Advanced Threat Protection)
- Microsoft Defender for Office 365 (previously Office 365 Advanced Threat Protection)
- Microsoft Defender for Identity (previously Azure Advanced Threat Protection)
Key Benefits of Defender for Endpoint
The Advanced Hunting feature supplies a decent library of queries either provided by the tool or developed by the security community and available on Github. The interactive reports and charts that summarize important KPIs and indicate how well the protection level of environment are useful.
Defender for Endpoint drastically increases your security through proactive and efficient threat detection and remediation management. To learn more, please request a discussion with our team or explore our Endpoint Management design and planning workshop offering.
What’s Next?
Join Mo Kamel and Chris Wilson for a deeper dive on the topic of Endpoint Management presented in partnership with the International Legal Technology Association (ILTA).
Monday, April 4th, 2022
Register here
