What is Zero Trust?
The ‘Zero Trust’ model is, in short, don’t trust, verify! A technology based defense to shore-up security vulnerabilities, the Zero Trust concept has quickly become the go-to security solution for organizations of all sizes.
In today’s threat landscape, multi-factor authentication (MFA) had become ubiquitous. The trend of adopting Passwordless MFA technology as part of a larger ‘Zero Trust’ strategy is gaining traction across future ready organizations. What replaces traditional “Passwords”? How can we leverage technology to eliminate the risks caused by human behaviors? CTO, Chris Owens shares the methodology employed by Kraft Kennedy to adopt a Zero Trust model in these session highlights from Establishing Trust in Zero Trust, delivered at LegalSEC Summit 2023 for the International Legal Technology Association.
Beginning the Zero Trust Journey
Reaching Zero Trust doesn’t happen overnight, the journey will be unique to your organization’s security environment. A good universal starting point is to begin with the creation of device policies and the implementation of device certificates.
A series of decisions will inform next steps, including: what it means for a device to be compliant. which applications are required and which are unauthorized and more. The goal is to tie a user to a device, and in doing so, establish better tracking capabilities and more detailed, useful logs.
The Future is Passwordless
One of the first milestones in the Zero Trust journey at Kraft Kennedy was the implementation of Windows Hello for Business. This enabled multi-factor unlock – users must verify two of the five available authentication factors to login: fingerprint, face, PIN, network, or FIDO key. Getting users familiar with biometric capabilities is essential to adopting a Zero Trust strategy.
In addition to biometric capabilities, we also introduced the Dynamic Lock feature. When a user takes their mobile device out of Bluetooth range, the computer locks itself. Though the user does not know their password, the ‘password’ still exists in the form of a 128 character key that is reset multiple times an hour. The user cannot change this password, and any attempt to do so will be logged. By separating the user from their password, we are better able to prevent phishing attacks, as the user will know that anyone asking for a password is not part of the organization.
By far the most difficult part of implementing a Zero Trust strategy at Kraft Kennedy was tracking down all the locations that still required users to enter a password. To determine where passwords were being entered, we created a script to run in Azure logs.
Say Goodbye to Active Directory
Our next challenge was eliminating Active Directory (AD) and replacing it with Intune. Replacing AD reduced login time from a few minutes to approximately six seconds. This took a bit more time and effort to implement, as there is not a 1:1 relationship between existing AD policies and Intune policies. At the same time, we transitioned from VPN to Azure AD Application Proxy. An additional benefit of Intune is that all browser-based applications that were previously only accessible on a PC, are now available on mobile devices.
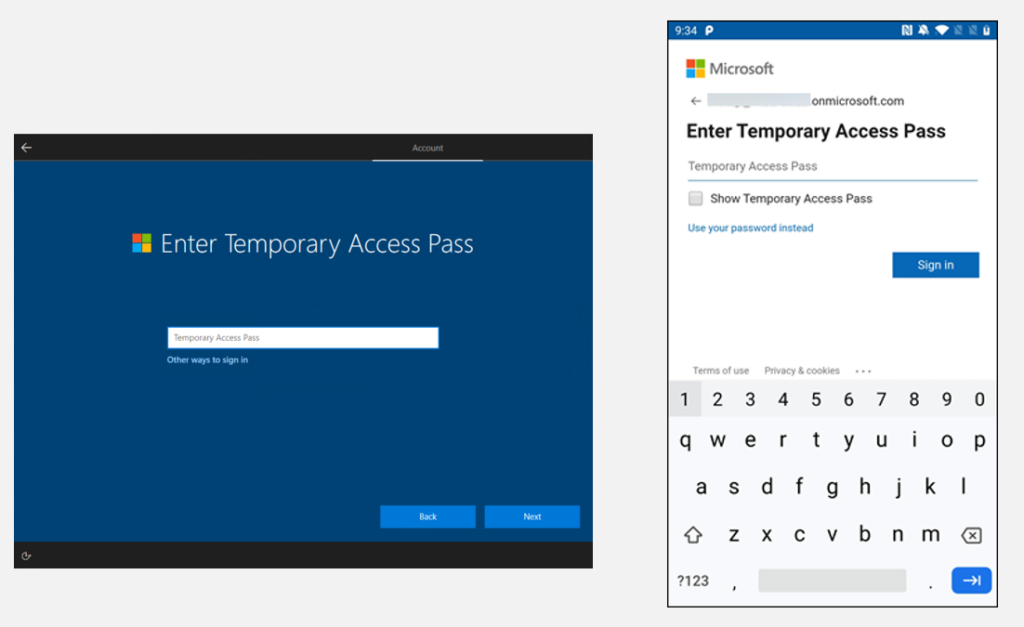
With our MFA and Intune policies in place, we shifted our focus to user enrollment. In keeping with the Zero Trust model, we implemented a Temporary Access Password for new device enrollment. New users receive a Temporary Access Password generated by the IT Support team. This password allows users to log into their first device, which then becomes a trusted machine. Once you have established a trusted device, that trust can be extended to other machines.
One notable downside is the inability of Microsoft to audit the Temporary Access Passwords. To solve for this internally at Kraft Kennedy, our Dev Ops team established a monitoring sequence. When a Temporary Access Password is generated, an email is sent to the user and our internal Risk Committee. As an additional layer of security, the internal team that manages the Temporary Access Password process, is restricted from disabling the monitoring sequence.
Conditional Access is Key
The final pillar of our Zero Trust strategy is perhaps the most important: creating Conditional Access policies. Conditional Access policies govern which known users and devices can access specified resources. One example of this is our MFA: Skip Trusted Network policy. Kraft Kennedy users logging into our firm network at one of office locations, do not need to verify multiple factors.
The Zero Trust Roadmap
The journey to Zero Trust will be unique for each organization. By adding key milestones to your technology roadmap (passwordless authentication, tying users to devices, eliminating Active Directory, creating conditional access policies…) future-focused firms will on the path to establishing Zero Trust.
To explore a Zero Trust strategy for your environment, please connect with the experts at Kraft Kennedy.