Setup and usage tips for Azure Information Protection
These are the default labels you get with Azure Information Protection (AIP).
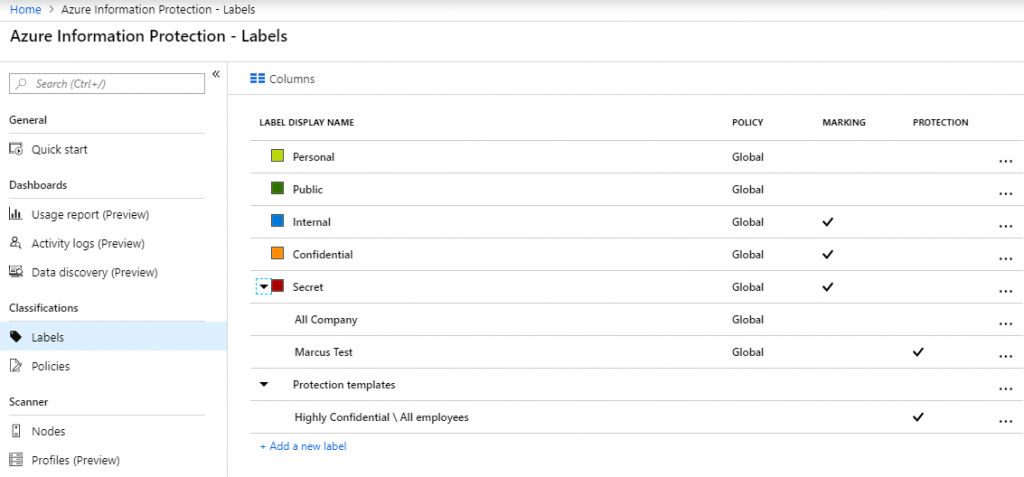
We recommend that you meet with your firm leaders to develop a classification and security plan. Similar to planning other systems like Document Management, try to focus on a simple and clear strategy. If you make it overly complex and cumbersome, user participation will suffer.
You can configure the default global policy or create group/user specific policies. Here are the options to consider:
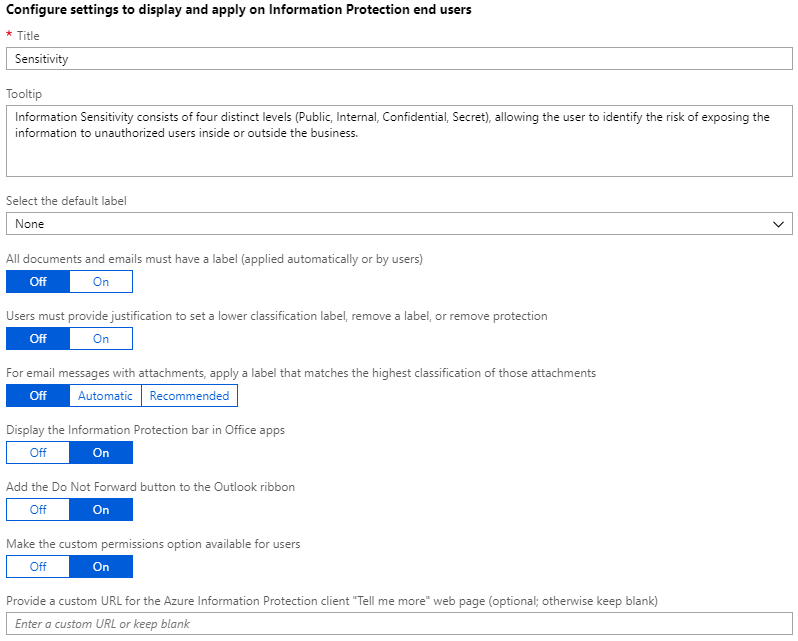
While many of the options above can add value and protection, they come at a cost of time and complexity. Make sure to do plenty of testing and gather feedback before deploying to your firm.
Through AIP, you can monitor usage as well. This is an important step in making sure your users stay engaged with the technology.
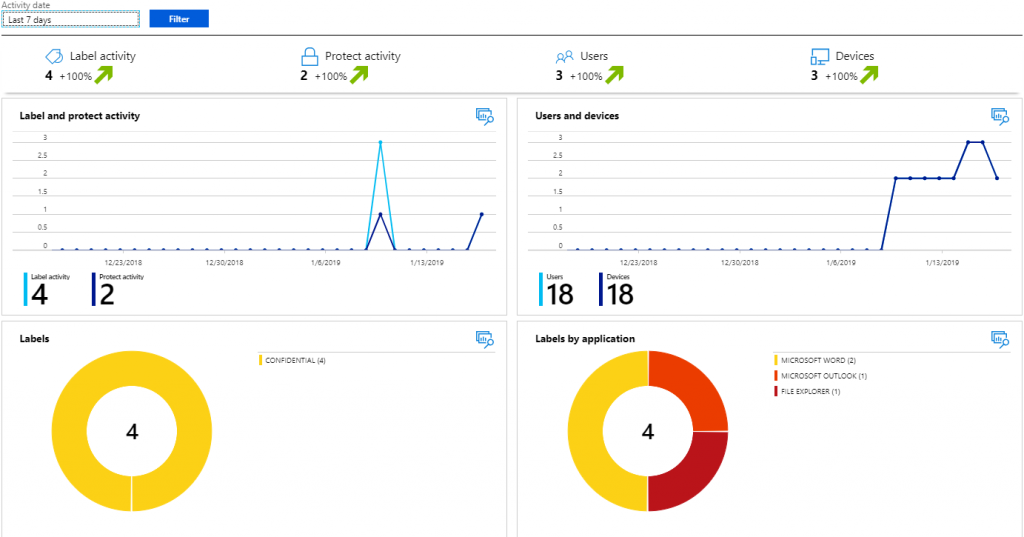
All of the data above is important to track. In my testing, I have selected
only the Confidential classification. If this were a production deployment, I would be concerned why none of the other labels were being used. For example, are they redundant or too complicated?
As an administrator, I can view the activity logs for AIP usage. For example, I can see this:
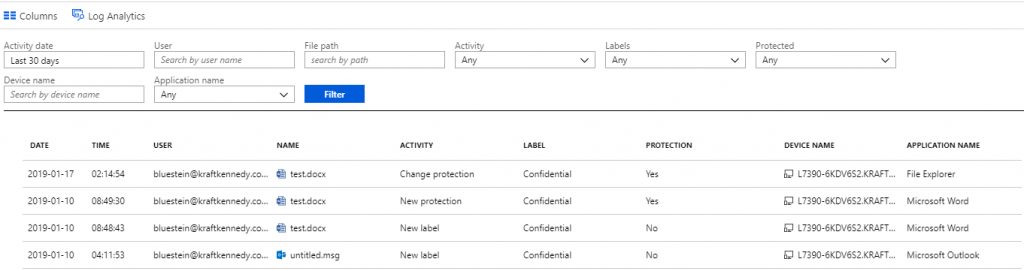
I can’t open or view content from this screen. That is, my administrator permissions do not bypass the security on the content.
There is much more to Azure Information Protection that I’d be happy to blog about! If you are interested in learning more, please comment below or drop us a line.
