A particularly aggressive virus announced its presence at one of the midsized Support Practice Group firms earlier this month when multiple user accounts suddenly became locked out in quick succession. The virus had infiltrated the firm and launched a brute-force attack in an attempt to crack account passwords. With the help of a network-wide scanner, the intrusion was traced to four machines, three of which were utility computers provided by service companies specializing in copying and postage printing. Those computers, having been installed by external companies, were never given antivirus protection or patched in accordance with the other workstations. The infected machines were quickly shut down to quarantine the virus and were later taken off the network to be cleaned.
The successful containment of what could have been a widespread network infection testifies to the effectiveness of multilayered threat protection policies and offers two important reminders about network administration:
First and foremost, it is important to regularly update Windows and install an antivirus program on every computer on a network. Although they are easy to overlook, even utility machines that are brought to a firm by a service provider to perform a specific function must conform to standard threat protection practices.
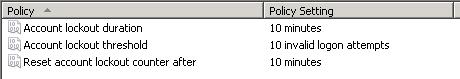
Second, we are reminded that enabling account lockout rules in group policy is an extremely simple and effective way to combat viruses. Locking out an account after five to ten incorrect password attempts even for a period of just ten minutes can render a brute-force attack ineffective and alert network administrators to the presence of a virus within minutes of first contact.
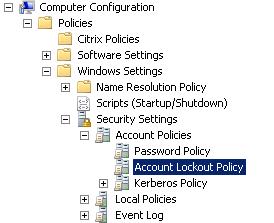
To enable account lockout rules on your domain, follow these simple steps:
- Open your Group Policy Management console and edit the group policy object where your network’s password policy is defined. Typically this is done at the domain level.
- Edit the account lockout policy, which should be located under Computer ConfigurationPoliciesWindows SettingsSecurity SettingsAccount Policies
- Set the maximum number of password attempts before lockout and the time period for which you would like to lock the account. The following are fairly standard values: