In the second part of this series on SCCM Desired Configuration Management, we began creating Configuration Items for the scenario of establishing a corporate laptop security baseline. We continue here with some more sophisticated queries to give you a sense of how one incrementally builds up a DCM baseline.
Configuration Items based on programmatic queries
Now that we’ve got the hang of basic validation checks, let’s try some more sophisticated tests using a bit of VBscript. The first one will verify that our anti-virus definitions file (we use Symantec in this example) has been updated within the past 7 days. Here’s how to set this up.
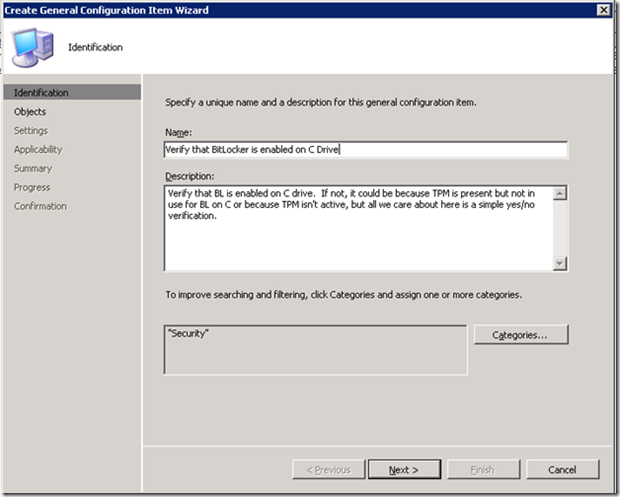
Right-click on the parent node (“Kraft & Kennedy” in our case) and select New > General Configuration Item. Fill in the dialog as follows:
![clip_image002[12]](/wp-content/uploads/images/clip_image00212_thumb4.jpg)
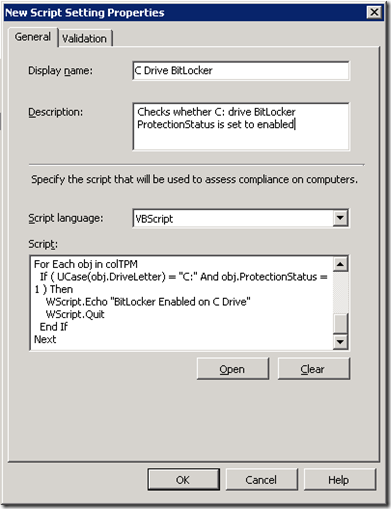
Click Next twice to get to Settings. This is the node where one can choose VBscript as a validation method. Click New > Script and fill in the dialog as follows. The VBscript we’ll use is:
Option Explicit
Dim VirusDefCfg, FileSys, FSO, LastModified, DateDifference, noSymantecPresent
VirusDefCfg = "C:ProgramDataSymantecDefinitionsVirusDefsdefinfo.dat"
noSymantecPresent = 9999
Set FileSys = CreateObject("Scripting.FileSystemObject")
Set FSO = CreateObject("Scripting.FileSystemObject")
If FileSys.FileExists(VirusDefCfg) <> True Then
WScript.Echo noSymantecPresent
WScript.Quit
End If
LastModified = FSO.GetFile(VirusDefCfg).DateLastModified
DateDifference = DateDiff(“d”, LastModified, Now())
WScript.Echo DateDifference
In a nutshell, we check that the desired file exists and, if so, obtain the number of days since the file was last updated. Whatever the result, we use WScript.Echo to report back to the caller. In this particular case, I’ve chosen the number 9999 as a surrogate to indicate that the A/V definitions file doesn’t exist, which would be bad news.
![clip_image004[10]](/wp-content/uploads/images/clip_image00410_thumb3.jpg)
Now let’s set up our validation: click Validation > Data Type = Integer, then click New and fill in the dialog as follows:
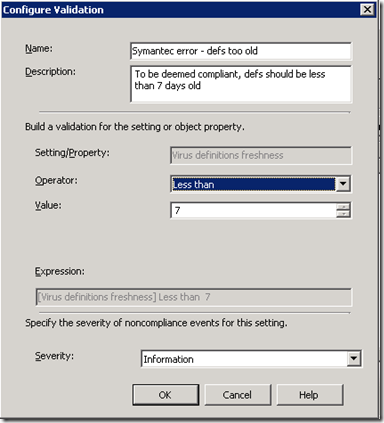
Click OK twice, then Next until you’re done.
We’ll create a final General Configuration Item using a VBscript for checking whether or not the laptop’s C: drive is encrypted with BitLocker. While this article isn’t intended as a VBscript or WMI primer, in brief, we’re checking the laptop’s Windows Management Instrumentation (WMI) repository to see if BitLocker is enabled on the C: drive and, if so, outputting a string that says so. For more info, this Microsoft article is a good starting point.
Practical note: since you can’t easily test or debug a VBscript inside DCM, you should develop your script first (using whatever means you’re accustomed to, e.g. command line or programmer IDE) and only when you know it works should you incorporate the script into a CI as we’re doing here.
Option Explicit
On Error Resume Next
Dim objWMI, obj, colTPM
Set objWMI = GetObject(“winmgmts:\.ROOTCIMv2SecurityMicrosoftVolumeEncryption”)
If Err <> 0 Then
Script.Quit
End If
Set colTPM = objWMI.ExecQuery (“Select * from Win32_EncryptableVolume”)
For Each obj in colTPM
If ( UCase(obj.DriveLetter) = “C:” And obj.ProtectionStatus = 1 ) Then
WScript.Echo “BitLocker Enabled on C Drive”
WScript.Quit
End If
Next
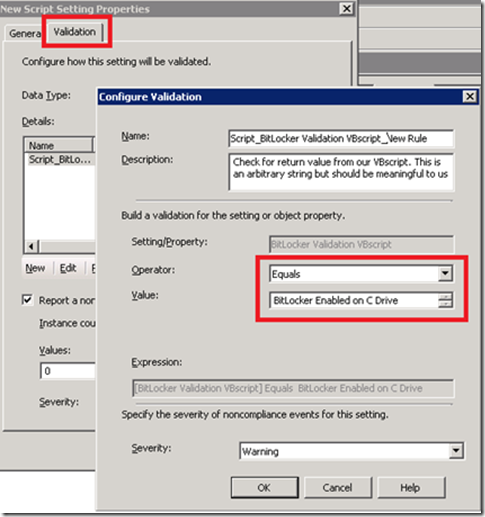
And here’s what the dialogs should look like:
Validation should be of Type = String and we’ll look for the phrase “BitLocker Enabled on C Drive”, which is how we set up our VBscript to report success:
Click through the OK prompts until you’re done. At this point, we have three CIs:
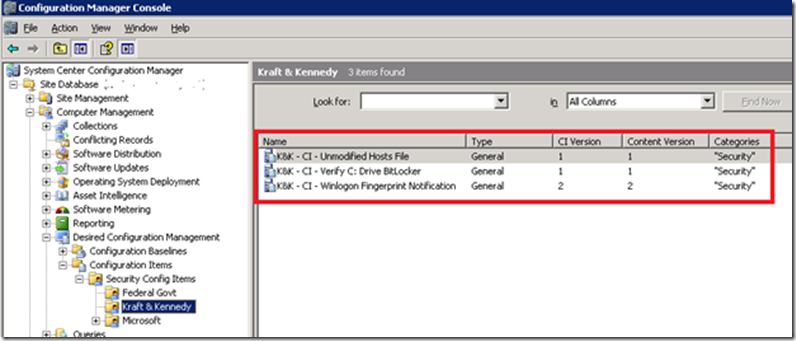
This concludes the creation of our Configuration Items. In the next part of the series, we’ll cover how to collect Configuration Items together in a baseline and then actually use the baseline to start monitoring and reporting on our company’s laptop security compliance.
