In the first four parts of this series, we covered SCCM Desired Configuration Management (DCM) in depth and went over the creation and use of custom baselines. Now that we understand the low-level details, it’s time to build on that foundation. Continuing our laptop security focus from last time, in this blog post we’ll look at how to use Microsoft’s Security Compliance Manager toolkit to feed security baselines into DCM.
Security Compliance Manager
One of Microsoft’s vaunted “Solution Accelerators,” Security Compliance Manager (SCM) is a freely-downloadable utility used by thousands of organizations for managing their computer security baselines. While there are third-party products that can do even more, SCM is effective in its own right and free is hard to beat. One can download recommended baselines from Microsoft for a variety of operating systems, import them into SCM, edit them and export them to a variety of formats. In addition, various third parties offer their own baselines and you can copy and build upon any of them within SCM.
I won’t go over how to obtain and install SCM — there is plenty of material on the web, including this intro video. At the time of writing, SCM 2.0 is nearing release and I’m using a final beta release.
SCM installs and runs on any workstation or server. By default it creates a local SQL 2008 Express instance and isn’t centralized in any way (though the baselines you export for use by SCCM will be copied to the central SCCM server). A simple option if you have multiple admins who will be using the tool is to install SCM on a server and remote into it when you need to work with the utility.
Out-of-the-box, SCM installs several Microsoft-vetted security baselines. These are read-only and must be cloned in order to make edits. You can duplicate the baselines by hand but SCM makes an initial batch for you when you install the utility, based on your organization name, as here with “Kraft Kennedy Baselines”:
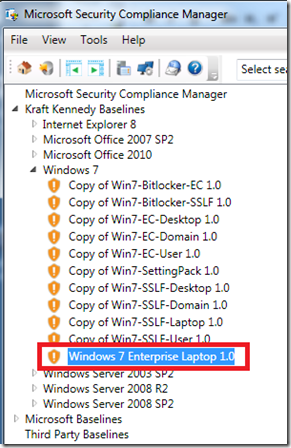
For our example, since this blog series has been focussed on laptop security we’ll work with Kraft Kennedy Baselines > Windows 7 > “Copy of Win7-EC-Laptop 1.0”, which I’ve renamed to make its purpose clearer:
This baseline is a collection of default security settings deemed by Microsoft (and vetted by thousands of organizations worldwide) to be reasonable options for a typical corporate laptop.
How to use SCM
SCM is principally an editing and organizing tool. To actually utilize SCM content, one exports baselines to a variety of formats, which are then consumed by other tools. In our case, we’ll export the settings to a DCM format (stored in a CAB file) suitable for use within SCCM. SCM can also output SCAP content (a widely-used industry format) or even Group Policy Objects.
There are several basic ways to use SCM in conjunction with SCCM DCM:
- Transit point – you can simply use SCM as a way station for downloading Microsoft’s recommended baselines, exporting them to DCM, then doing all editing work within DCM and dispensing with SCM.
- Library – you can perform all your edits within SCM and export the resultant baselines. DCM would just consume them and you would make no further edits: SCM is this thus your master library.
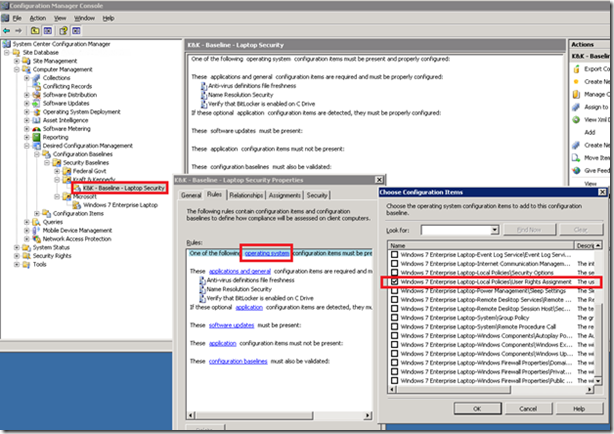
- Pick & choose — regardless of how you store and edit baselines, you can use them “as is” or pick and choose individual DCM configuration items to re-use within your own custom DCM baselines. You might do this both because there are hundreds of settings, not all of which you may be interested in, and also because Microsoft has already done the heavy lifting and figured out the validation queries. Recall from last time that devising these queries, some of them involving VBscript and WMI, takes some work, so if Microsoft has already done it for us, we shouldn’t be above borrowing their code. That’s actually what we’ll be doing here.
I usually try approach #1 first: utilize an entire Microsoft baseline, import it into DCM, assign it to an SCCM collection and see what pops up in the compliance report. This is the quickest way to get a sense of how a baseline works and where your organization’s systems stand with respect to it. At that point, you may decide to modify certain settings within the library (approach #2) when creating your production baselines.
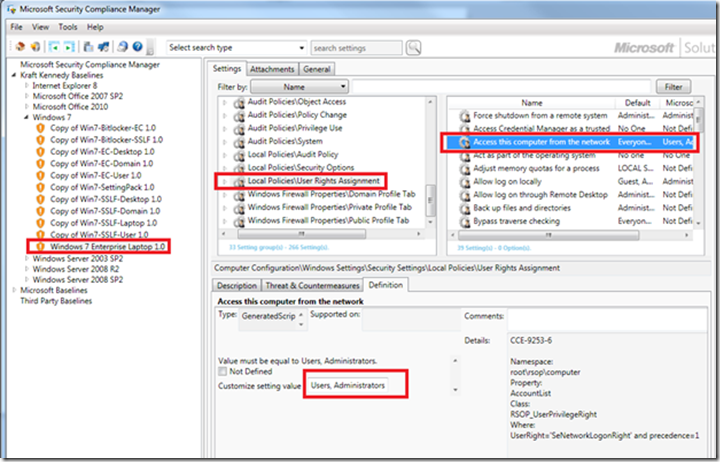
In the present case, I discovered that our organization was actually stricter than the baseline when it came to a specific setting:
Local Policies User Rights Assignment Access this computer from the network
Since we varied from the baseline, however, we were marked as “non-compliant.” Here is the setting in question:
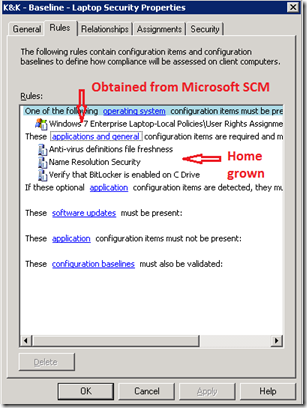
In our case, we don’t allow non-admins to access laptops from the network so I chose to customize this setting using our local requirements. I’ve left Microsoft’s other compliance recommendations as is and in fact we’re not even going to use them – when we convert the SCM format into DCM-consumable content, each of the settings groups is converted into a separate DCM Configuration Item and I only plan to pick the “Local Policies User Rights Assignment” item.
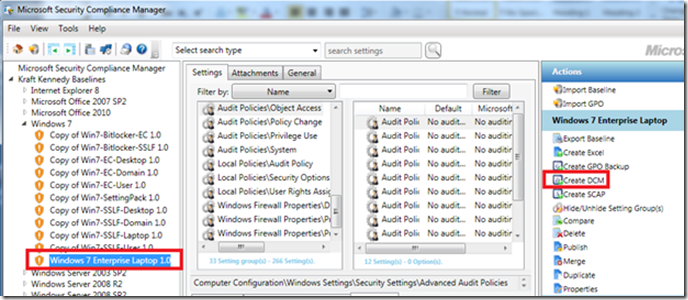
Getting back to the mechanics, here is how to export an SCM baseline for use by DCM:
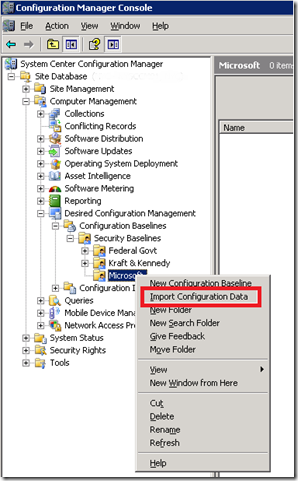
The Create DCM option outputs a *.cab file. Copy this CAB file to the SCCM server and right-click import it to the desired node within DCM. In a previous blog post, we had created a DCM folder for Microsoft and we’ll use that here:
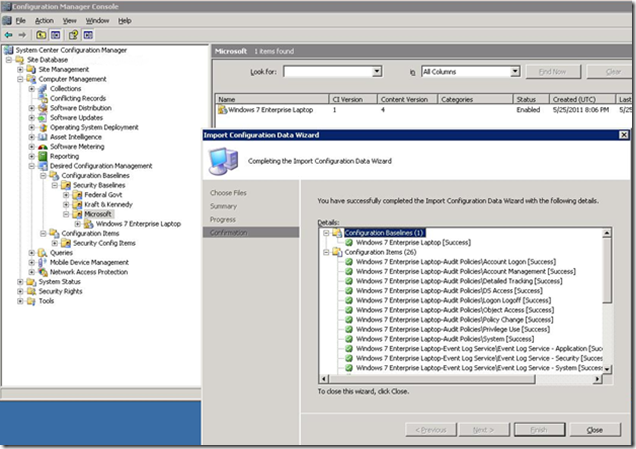
Note in the next screenshot that two kinds of DCM objects, Baseline and Configuration Items, were imported:
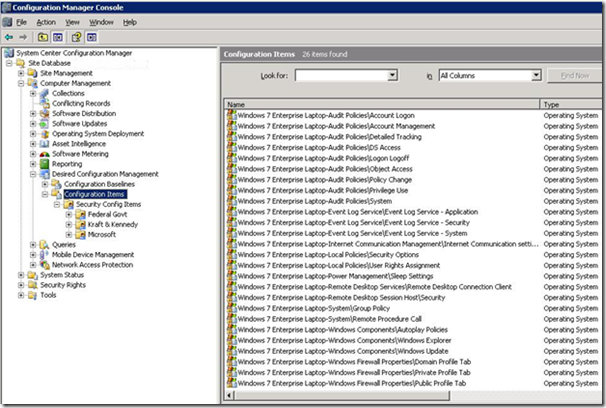
While the Baseline is in the place we imported it, the CIs are in the Configuration Items root node:
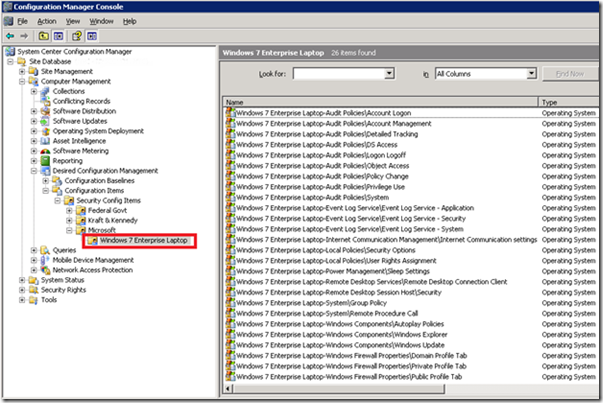
For the sake of keeping things organized, I created a new folder and drag/drop moved the CIs there:
As discussed previously, the first time through I like to just assign an entire baseline to a test/dev collection and see what the report shows. Then I cherry-pick specific Configuration Items or validation tricks from Microsoft’s baseline and re-use them in my own custom baselines. That’s what we’ll do here: we’ll add a single additional CI to the “K&K – Baseline – Laptop Security” baseline that we created last time. The CIs we just imported from SCM are classified by Microsoft as type “operating system” and here I’m picking that “User Rights Assignment” CI we edited earlier in SCM:
To recap what we just did, we combined two tools: Microsoft’s Security Compliance Manager (SCM) and SCCM Desired Configuration Management (DCM). Then we enhanced our own homegrown laptop SCCM DCM security baseline by sprinkling in a bit of magic dust we dug up from one of Microsoft’s SCM baselines:
The first four parts of this series have demonstrated the mechanics of creating SCCM DCM baselines. As you can see, once you get the hang of things it’s easy to iteratively build up your baselines over time until you have quite a sophisticated set of compliance checks.
In the final part of this series, we’ll look at a non-security baseline and then discuss a nifty technique for automatically bringing PCs that have suffered from configuration drift back into line through self-healing.