In the second and third parts of this series on SCCM Desired Configuration Management, we created some Configuration Items (CIs) that showcased a variety of validation techniques. Now we’re ready to turn the individual CIs into a baseline and begin using it for compliance reporting.
Creating the Baseline
Whew, creating those CIs seemed like a lot of work. Actually, it’s easy once you’ve gotten the hang of it. But we’re not quite done — now it’s time to collect these CIs together into a Baseline. Go into the DCM Configuration Baselines node, right-click the folder where you want to create your new Baseline and select New Configuration Baseline:
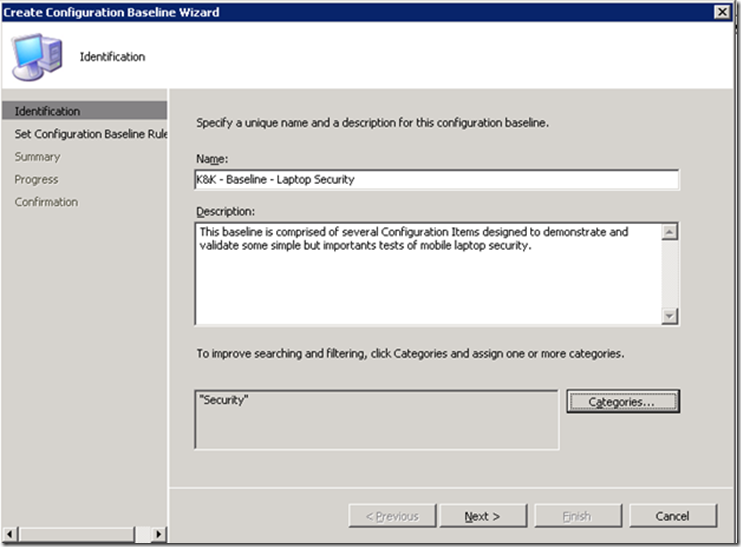
I’ve filled in the dialog with some basic info:
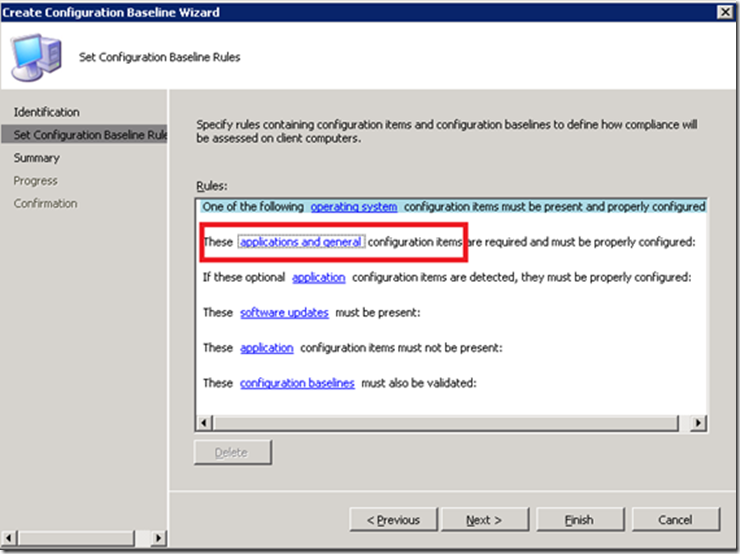
After clicking Next you arrive at a screen that allows you to pick your validation criteria. In this case, since the CIs we created earlier were of the General variety, we’ll choose “applications and general configuration items”:
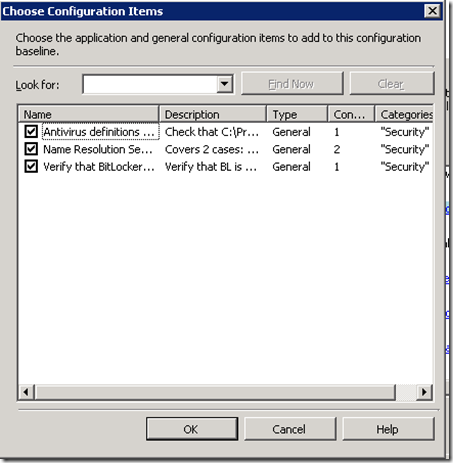
A list of available CIs will appear — in this case we’ve only created three CIs but in practice you’re likely to have dozens of CIs and will need to pick and choose. Here I’m selecting all three:
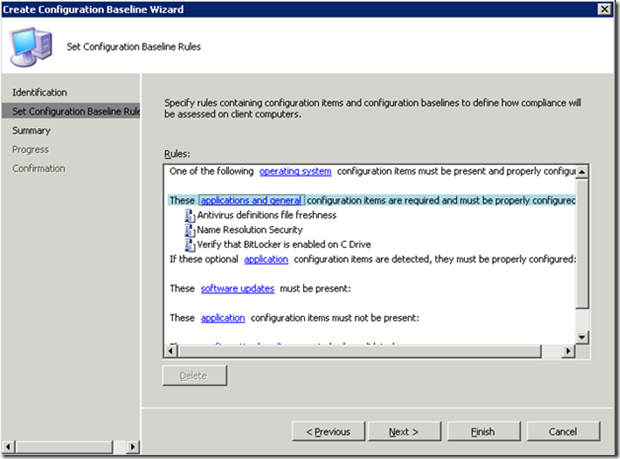
Click OK to arrive at this screen:
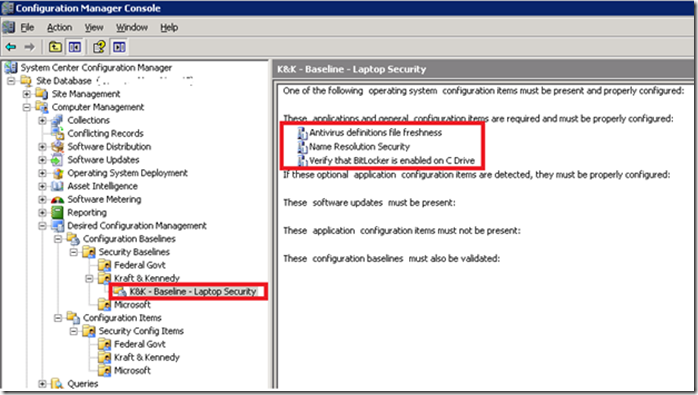
Click Finish. We’ve created our first Baseline, which contains three CIs:
Assign baseline to a collection
Finally, to actually make use of the baseline we’ll assign it to an SCCM collection:
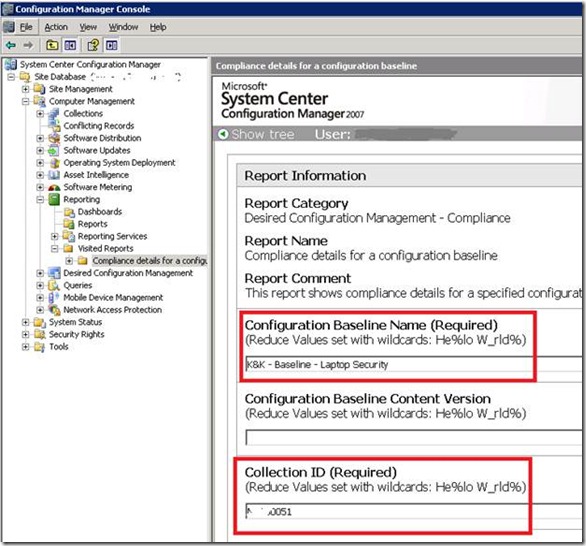
Pick a collection that makes sense to you. In my case, I first targeted a test/dev collection consisting solely of my own laptop (to verify that the basics worked), then tried a larger collection to shake out the final bugs and finally moved on to an enterprise collection that consists of all of the firm’s laptops. The default assessment schedule of 3 days is probably fine — I’ve found that clients start processing new DCM baselines fairly quickly (the 3 day schedule only applies once the version IDs of the baselines and CIs are no longer changing, which they do frequently while you’re testing). Wait a few minutes and pick a report such as “Compliance details for a configuration baseline”:
Right-click to run the report and fill in the required parameters, e.g.
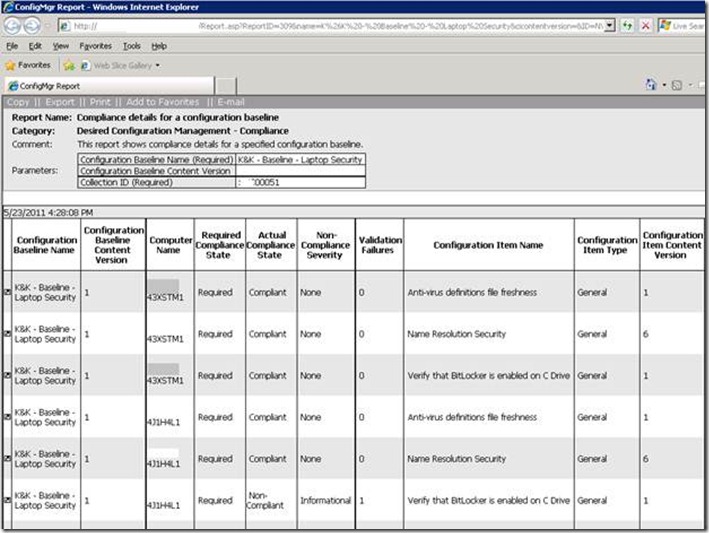
In the screenshot below, the compliance state for each of our three CIs is shown for two distinct laptops. In this case, one of the laptops appears not to be using BitLocker – potentially actionable intelligence for our firm’s administrators.
This concludes our look at the fundamentals of using DCM. In the final two parts of this series, we’ll take up the use of third-party baselines and the use of DCM to provide a self-healing capability through the creation of a dynamic SCCM collection.
![clip_image002[14]](/wp-content/uploads/images/clip_image00214_thumb1.jpg)
![clip_image002[16]](/wp-content/uploads/images/clip_image00216_thumb1.jpg)
![clip_image004[12]](/wp-content/uploads/images/clip_image00412_thumb2.jpg)