We have recently been locking down systems to protect them from the DROWN Attack vulnerability. The process involves removing the unsecured SSL protocols and SSL ciphers and has generally been straightforward.
Today, however, when locking down a Citrix NetScaler 11.x VPX appliance with a locally installed Web Interface, we kept running into the issue with the blank AGESSO.JSP file after logging into the web site. In most cases we recommend clients move the Web Interface role off any NetScaler implementation, in favor of Citrix StoreFront, but we do still see this setup from time to time.
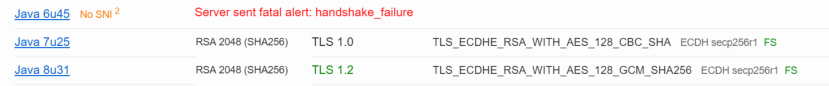
The blank AGESSO.JSP is a reasonably common issue, with many solutions, none of which worked today. Eventually we narrowed down the problem to us missing the following cipher on the NetScaler Gateway Virtual Server: SSL3-DES-CBC3-SHA. With this cipher missing, the Java Web Interface running on the Citrix NetScaler appliance didn’t trust the installed NetScaler Gateway.
The output from SSL Labs showed the following differences:
Without the SSL3-DES-CBC3-SHA cipher included
With the SSL3-DES-CBC3-SHA cipher included
It looked like the NetScaler Web Interface is still running Java 6.x that doesn’t trust the Access Gateway.
So, if a client cannot migrate to StoreFront, my new best practice for the SSL ciphers on a NetScaler Gateway VPX (running version NetScaler Build 11.0-65.31 or later) are the following:
bind ssl cipher vpx-cipher-list
bind ssl cipher vpx-cipher-list -cipherName TLS1.2-ECDHE-RSA-AES256-GCM-SHA384
bind ssl cipher vpx-cipher-list -cipherName TLS1.2-ECDHE-RSA-AES128-GCM-SHA256
bind ssl cipher vpx-cipher-list -cipherName TLS1.2-ECDHE-RSA-AES-256-SHA384
bind ssl cipher vpx-cipher-list -cipherName TLS1.2-ECDHE-RSA-AES-128-SHA256
bind ssl cipher vpx-cipher-list -cipherName TLS1-ECDHE-RSA-AES256-SHA
bind ssl cipher vpx-cipher-list -cipherName TLS1-ECDHE-RSA-AES128-SHA
bind ssl cipher vpx-cipher-list -cipherName TLS1.2-AES256-GCM-SHA384
bind ssl cipher vpx-cipher-list -cipherName TLS1.2-AES128-GCM-SHA256
bind ssl cipher vpx-cipher-list -cipherName SSL3-DES-CBC3-SHA