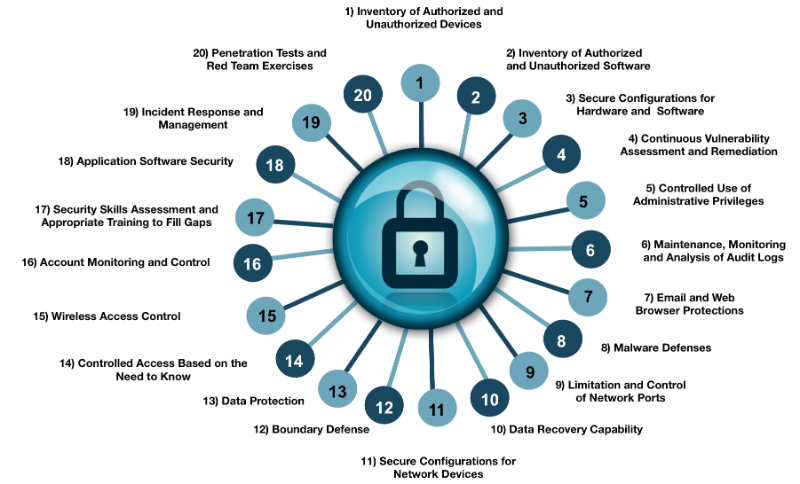
The Center for Internet Security (CIS) Critical Security Controls is a security standard centered on a list of 20 technical controls that organizations can implement to better defend themselves from cyber-attacks. The controls take a prioritized approach, making them different from security risk management frameworks such as NIST 800-53, ISO 27001, and COBIT. These well-known risk management frameworks are meant to do exactly that, manage risk. They do not prioritize control implementation, leaving it up to the organization to decide the level of importance for each control.
I had the pleasure of attending the SANS SEC566 class in early December 2016, which focuses on the Critical Security Controls. The class discussed each control in depth, giving context to the whys and hows. Each control was discussed in terms of business goals alongside a case study of a breach that could have been prevented had the control been implemented. We learned appropriate defensive measures and sensors for each control. Equally important are the specific metrics of each control, used to measure its overall effectiveness. The goal of each control is to have a high degree of automation, leaving us mere humans a less daunting task of reviewing the huge influx of data received from each control.
Organizations often forget or do not want to admit that security is a never-ending process. The only way to start “winning” against attackers is to measure your risk management program. Without having data to measure the program’s effectiveness, you are merely swinging in the dark, letting vendors dictate where your money is going rather than basing spending decisions on facts, meaning data. Businesses need to keep in mind that risk management is a business problem, not an information technology problem. IT departments are typically focused on keeping systems healthy, ensuring user productivity, implementing new technologies, etc. The focus here is systems, applications, and networking. Information Security has a different focus, however, which is protecting the business’s data. The technologies put in place by IT departments are merely a way to access the data, which is where the true value of a company lies. Therefore, managing the risk introduced by information systems needs to be understood by the business and managed accordingly. A business should look at its information security program in the order of people, process, and technology. If you buy the best technology currently on the market and don’t have skilled people to run it and analyze the data, you are wasting your money and ultimately have done little in securing the business. Turning a blind eye to risk management and security operations will most certainly lead to compromised data and, depending on the type of information, could lead to large regulatory fines or costly lawsuits.
To give some additional context into the Critical Controls, let’s focus on Control 1, as this is foundational even in the popular risk management frameworks. Control 1 focuses on hardware asset management, including information management. While this seems to be a simple concept, it is necessary to understand the business assets in order to build out a risk management process. To start with, how can you protect an asset that you do not even know is sitting on your network? Similarly, how can you protect information within your network if you do not understand where the data is? While this seems very basic, many organizations cannot answer this question with 100% certainty. When conducting security assessments for organizations, it is almost guaranteed that we find older legacy systems that the client forgot were still on the network.
Control 1 takes this simple concept further. When we think about authentication we typically think about our usernames and passwords, i.e., user authentication. However, Control 1 asks that we authenticate at the network layer. By using Network Level Authentication (NLA), which verifies that a system belongs on the network, we can ensure two things. One, no system that does not have the certificate will be allowed on the network. Two, authorized but not fully configured systems that could potentially introduce risk to the environment are not allowed on the network. This second point speaks to the more probable scenario, as there isn’t a great deal of evidence of attackers physically going into buildings to plant devices. With the dawn of virtualization, IT teams are able to quickly deploy new servers for testing or upgrading, which are often left in half-configured, insecure states. While this is not the full extent of Control 1, it does offer some insight into the thought behind the controls.
By working through the Critical Controls, an organization can implement the “offense leads defense” approach. Attackers are constantly leveraging different attack methods and the Critical Controls prioritize defensive measures based on attacker patterns. I highly recommend that all organizations take a good look at the Critical Controls to see how to build a strong foundation for assessing risk to the business in an orderly fashion.