Scenario: your company’s management is concerned about the security of the firm’s laptops. They’re mobile, people use them in public, and there’s the inevitable risk of loss or theft. In the back of your mind, several things would allow you to rest easier at night:
- You don’t want the laptop participating in peer-to-peer (P2P) activities whether it’s onsite or off the corporate LAN
- You are concerned about a malware hijacking technique that short-circuits name lookups for websites such as update.microsoft.com by replacing a PC’s “hosts” file with a Trojan version
- Anti-virus definitions should be up-to-date
- You’re using Windows 7 and want to be sure that BitLocker drive encryption is used on the C: drive
There are many other ideas, but you’ve settled on these. All well and good, but how do you translate good intentions into an actionable DCM baseline? We’ll assume that you’ve seen or used SCCM before but are unfamiliar with DCM. Not to worry, let’s dive in.
Open up ConfigMgr (the SCCM 2007 management utility). In DCM, one performs two basic tasks: setting up baselines and running reports. You do setup and configuration work in the Desired Configuration Management node, highlighted below:
To actually utilize your baselines, you assign them to SCCM Collections and then use SCCM’s rich reporting capabilities. Here are some of the built-in DCM reports available:
![clip_image004[4]](/wp-content/uploads/images/clip_image0044_thumb3.jpg)
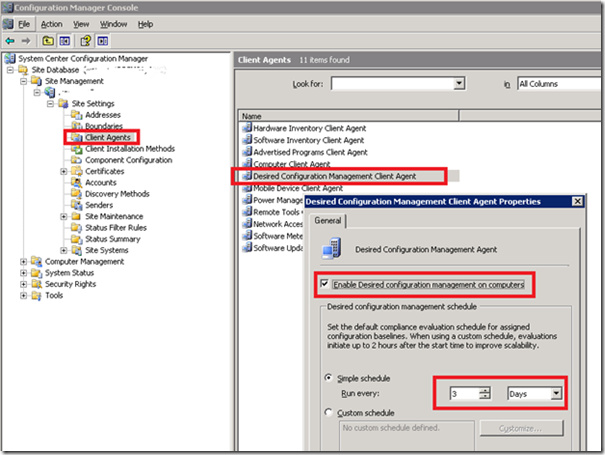
Finally, SCCM clients have a DCM agent that actually evaluates the baselines and reports back up to the SCCM server. You can enable and configure the agent under the Site Management node. Right-click the agent to bring up its properties. Here we’ve enabled the agent and set it to run every 3 days:
Going back to the DCM node, notice that there are two categories, Configuration Baselines and Configuration Items. Here’s the 30,000 foot view of what you need to do:
- You create one or more Configuration Items
- Configurations Items contain one or more criteria for which you decide what constitutes proper Validation
- These Configuration Items are put into a Configuration Baseline
- You assign this baseline to an SCCM Collection
- The DCM agents on PCs that are members of the collection run the baseline and report back to the SCCM server
Enough theory — in the second part of this series we’ll create and configure several DCM Configuration Items.
![clip_image002[4]](/wp-content/uploads/images/clip_image0024_thumb2.jpg)