In the last few years wireless technology has become an increasingly popular method of network access for employees and guests alike. It is almost expected of some businesses, such as cafes and libraries, to have wireless networks to which guests can connect. New York City has even announced that they will be converting 7,000 telephone booths into wireless access points over the next few years.
At Kraft Kennedy we have seen a large uptick in the need for wireless networks across businesses of all sizes. Clients and guests regularly request the ability to quickly access the internet, their e-mail, and continue day-to-day business remotely. Employees also like to bring in their own devices, such as phones and tablets, that need access to the internet.
We use Meraki’s line of wireless products to offer cost-effective, competitive, and easily managed wireless solutions. Due to their ease of use, flexible management, and the granular configuration options, Meraki has become the go-to solution for our wireless implementations. Initial configuration and installation is a snap. All device configuration is managed through a web-based dashboard which allows monitoring and management from anywhere in the world. From a business standpoint, one of the biggest draws of Meraki is its ability to easily create in-depth firewall rules and traffic-shaping policies. Meraki devices use deep-packet inspection on all network traffic which provides IT and management with detailed traffic analysis on several levels. Detailed traffic analysis includes multiple elements, such as IP addresses, host names, and port ranges to identify traffic flow. This allows administrators to limit or block traffic to unneeded or unwanted applications, such as Netflix or music streaming, which allows for more throughput for business applications.
To block traffic the Meraki dashboard allows for Layer 3 and Layer 7 firewall rules. Layer 3 refers to the IP address that the traffic is coming from, while Layer 7 inspects the packet and matches it against different known traffic types. This is great for administrators who may not be too familiar with traditional firewalls but still want an easy way to block unneeded traffic.
The above screenshot shows a few of the Layer 3 firewall rules. The last two are defaults on Meraki devices, where an administrator would either allow Wireless clients accessing LAN if the network is for internal clients, or deny all traffic access the LAN for a network catering to guests.
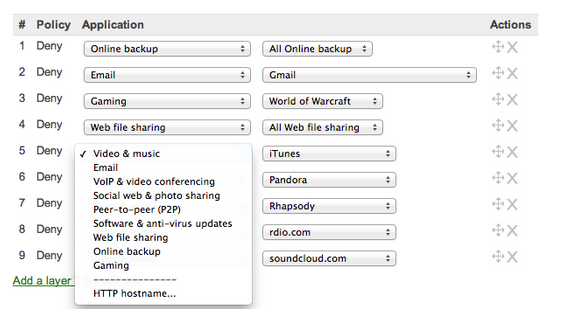
What I find most interesting about Meraki devices is their ability to analyze known traffic patterns and use this to allow for Layer 7 firewall rules. The above screenshot shows some of the different rules administrators can create to block traffic based on application-specific protocols or broader groups such as “Gaming” or “Peer-to-peer.” This allows administrators to be as granular as they want to be. For example, they can allow clients to access iTunes but block all traffic to Rhapsody.
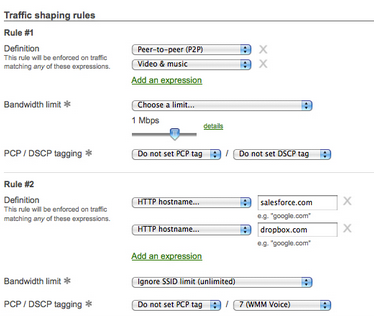
The Meraki console also allows for traffic shaping, which throttles traffic to non-business applications such as music and gaming and prioritizes business applications such as voice or video conferencing. This ensures that business application performance is not compromised and also allows users to listen to music while they work. Administrators can shape traffic in a few ways by defining rules based on application categories integrated into the Meraki dashboard or adding custom rules by specifying HTTP hostnames, port numbers, IP ranges or a combination of these. An action is then applied to these rule definitions. For example, to throttle traffic to Pandora, administrators would select Pandora from the drop-down menu and then specify the maximum allowed throughput to the application.
The above traffic shaping policy limits P2P and all video and music traffic to a maximum of 1 Mbps for all users while prioritizing traffic to “salesforce.com” and “dropbox.com” and allowing unlimited bandwdth to these applications.
The Meraki dashboard is cloud-based and constantly updated. New P2P and social media applications are quickly analyzed and added to the dashboard, so administrators are always up to date. Firewall rules and traffic shaping are just a few aspects of creating a secure and business-oriented wireless network. Firms looking to implement a new network or upgrade their existing one should start looking into Meraki.
In conclusion, wireless has become a considerably prolific and necessary technology in today’s business environment. Enabling employees and guests with an easily accessed internet connection improves business productivity and enhances communication. When looking into different solutions for wireless access Meraki should be on your list.